Description of the Windows Update Standalone Installer in Windows
Windows Vista Home Basic Windows Vista Home Premium Windows Vista Ultimate Windows Vista Business Windows Vista Enterprise Windows Vista Starter Windows Server 2008 Datacenter Windows Server 2008 Enterprise Windows Server 2008 Standard Windows Server 2008 for Itanium-Based Systems Windows 7 Home Basic Windows 7 Home Premium Windows 7 Professional Windows 7 Ultimate Windows Server 2008 R2 Datacenter Windows Server 2008 R2 Enterprise Windows Server 2008 R2 Standard Windows 8 Windows 8 Enterprise Windows 8 Pro Windows Server 2012 Datacenter Windows Server 2012 Datacenter Windows Server 2012 Essentials Windows Server 2012 Foundation Windows Server 2012 Foundation Windows Server 2012 Standard Windows Server 2012 Standard Windows 8.1 Enterprise Windows 8.1 Pro Windows 8.1 Windows Server 2012 R2 Datacenter Windows Server 2012 R2 Standard Windows Server 2012 R2 Essentials Windows Server 2012 R2 Foundation Windows 10 More. Less
Introduction
This article describes the Windows Update Standalone Installer (Wusa.exe) in the following Windows operating systems:
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows Server 2008 R2
- Windows 8
- Windows Server 2012
- Windows 8.1
- Windows Server 2012 R2
- Windows 10
- Windows Server 2016 Technical Preview
The Wusa.exe file is in the %windir%\System32 folder. The Windows Update Standalone Installer uses the Windows Update Agent API to install update packages. Update packages have an .msu file name extension. The .msu file name extension is associated with the Windows Update Standalone Installer.
More Information
An .msu file contains the following contents.
Windows Update metadata
Describes each update package that the .msu file contains.
One or more .cab files
Each .cab file represents one update.
This .xml file describes the .msu update package. Wusa.exe uses the .xml file when you perform an unattended installation of the update by using the Package Manager tool (Pkgmgr.exe).
For example, you download hotfix 934307. The Windows6.0-KB934307-x86.msu file is in the C:\934307 folder. You type the following command at a command prompt to expand the .msu file to a temporary folder:
expand -f:* “C:\934307\Windows6.0-KB934307-x86.msu” %TEMP%
Then, you type the following command at a command prompt:
A properties file
This file contains string properties that Wusa.exe uses. For example, this file contains the title of the associated article in the Microsoft Knowledge Base.
When you use Wusa.exe to install an update package, Wusa.exe expands the contents of the .msu file to a temporary folder. Then, Wusa.exe performs the following steps:
- Wusa.exe uses the Windows Update metadata in the .msu file to search for applicable updates.
- Wusa.exe copies the contents of the applicable updates to the Windows Update sandbox. The Windows Update sandbox is a protected folder.
- Wusa.exe calls the appropriate function in the Windows Update Agent API according to the mode in which you start Wusa.exe.
- When the Windows Update wizard finishes the installation, the Windows Update Agent API returns a status. Then, Wusa.exe works synchronously with the Windows Update Agent API.
Note Each update in an .msu update package is installed in a separate session. Only one instance of Wusa.exe runs when you use Wusa.exe. Wusa.exe does not change the contents of the updates in .msu files. The Windows Update infrastructure performs the required actions according to the contents of the update.
When you start Wusa.exe in interactive mode, a welcome screen displays high-level information about the update. If you continue to install the update, Wusa.exe calls the appropriate function in the Windows Update Agent API to start the Windows Update wizard. The Windows Update wizard displays the Microsoft Software License Terms that are associated with the update package. Wusa.exe calls the Windows Update Agent API to continue the installation. Then, Wusa.exe waits until the Windows Update wizard finishes the installation.
To install an .msu update package, run Wusa.exe together with the full path of the file.
For example, if the Windows6.0-KB934307-x86.msu file is in the D:\934307 folder, type the following command at a command prompt to install the update package:
wusa.exe d:\934307\Windows6.0-KB934307-x86.msuYou can also double-click the .msu file to install the update package.
You can use Wusa.exe to uninstall an update in Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012.
Note You cannot use Wusa.exe to uninstall updates in Windows Vista or Windows Server 2008. You can use Windows Defender Software Explorer to manually uninstall the updates. For more information about Software Explorer, go to the following Microsoft website:
Using Software Explorer in Windows Defender
You can use the following switches together with Wusa.exe.
Run Wusa.exe in quiet mode without user interaction. When the tool runs in quiet mode, it runs without user interaction. The computer restarts if this is required.
For example, if the Windows6.0-KB934307-x86.msu file is in the D:\934307 folder, type the following command at a command prompt to install the update package without user interaction:
wusa.exe d:\934307\Windows6.0-KB934307-x86.msu /quiet
Note When you use this switch, the Microsoft Software License Terms do not appear.
Prevents Wusa.exe from restarting the computer. The /norestart switch is ignored if the /quiet switch is not present. If you run Wusa.exe together with these two switches, you must manually restart the operating system after the installation is complete if the installation requires you to restart the computer.
For example, if the Windows6.0-KB934307-x86.msu file is in the D:\934307 folder, type the following command at a command prompt to install the update package:
wusa.exe D:\934307\Windows6.0-KB934307-x86.msu /quiet /norestart
Uninstalls the specified package or KB number.
Specifies the package to be uninstalled by using its KB number. Can be passed only together with the /uninstall switch.
Wusa.exe extracts the package contents to a destination folder.
When this switch is combined with the /quiet switch, Wusa.exe prompts you before it begins a restart for install and uninstall operations.
When this switch is combined with the /quiet switch, Wusa.exe forcibly closes applications and then begins a restart.
Note The .msu files can be installed to an offline image by using the DISM.exe /Add-Package option together with the Windows 7 or Windows 8 OEM Preinstallation Kit (OPK) or the Windows Automated Installation Kit (AIK). For more information, go to the following Microsoft TechNet website:
Operating System Package Servicing Command-Line Options
To view the Windows Update Standalone Installer event log, follow these steps:

-
Click Start , type event viewer in the Start Search box, and then click Event Viewer in the Programs list. In Windows 8 and Windows Server 2012, on the Start screen, type event viewer, click Settings, and then click View event logs under Settings.

If you are prompted for an administrator password or for confirmation, type the password, or click Continue.
In Event Viewer, expand Windows Logs, and then click Setup.
Утилита Windows Update MiniTool

01.10.2018

Alex Kornev

Windows 10, Утилиты

комментариев 15
Попалась на глаза, как мне кажется, полезная утилита для Windows 10, а именно Windows Update MiniTool. Программа предназначена для исправления урезанного функционала Windows Update в Windows 10.
Думаю, все уже успели заметить сильно урезанный функционал службы проверки и установки обновлений в Windows 10 по сравнению с предыдущими версиями Windows ( к примеру, нельзя скрывать обновления и пр.). Наверно, для домашних пользователей отсутствие инструмента управления обновлениями и не имеет особого значения, но для администраторов и опытных пользователей это существенная проблема.
В общем, группа товарищей решила исправить данную «оплошность» Microsoft и написала небольшую утилиту Windows Update MiniTool, которая возвращает привычный функционал установки обновлений. Утилита использует стандартную инфраструктуру Windows Update, а не списки обновлений на сторонних ресурсах.
Windows Update MiniTool позволяет:
- Выполнять проверка обновлений
- Скачивание обновлений
- Установку обновлений
- Удаление установленных обновлений
- Скрывать нежелательных обновлений
- Получать прямые ссылки на *.cab/*.exe/*.psf файлы обновлений
- Просматривать историю обновлений
- Настройка автоматических обновлений
- Работает на ОС начиная от Windows XP до Windows 10
Примечание. Утилита позволяет делать то же, что и сторонний модуль PowerShell PSWindowsUpdate, но в гораздо более удобном графическом интерфейсе.
Программа портабельная, есть 2 версии: 32-х и 64-х битная. Ссылки на актуальную версию и языковые пакеты есть на сайте: http://forum.ru-board.com/topic.cgi?forum=5&topic=48142#2
Вот несколько скриншотов, показывающих функционал программы. В общем то все должно быть понятным из скриншотов. Интерфейс разделен на две панели: в правой содержится список обновлений, в левой – категории и инструмента управления
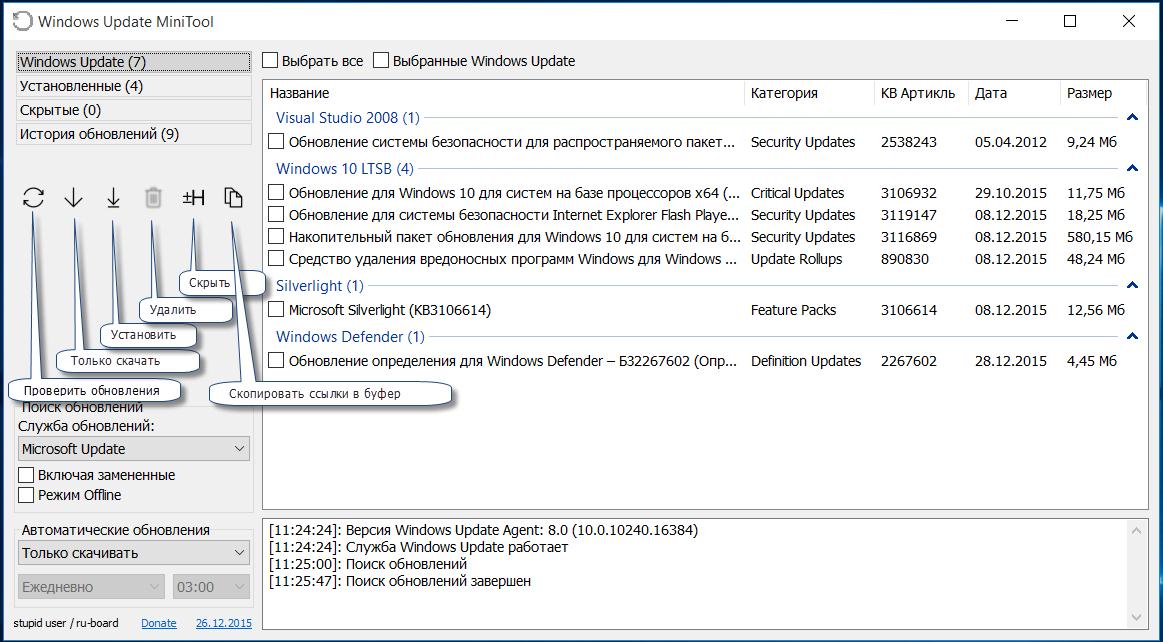
Настройка откуда брать обновления:
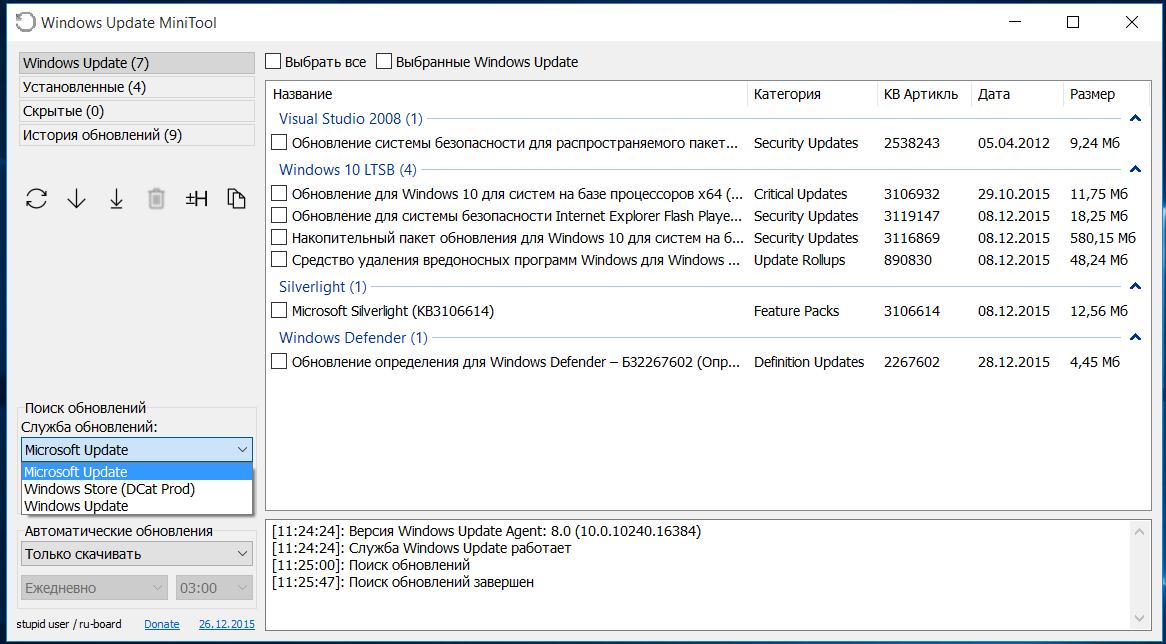
Настройки режима закачки и установки обновлений:
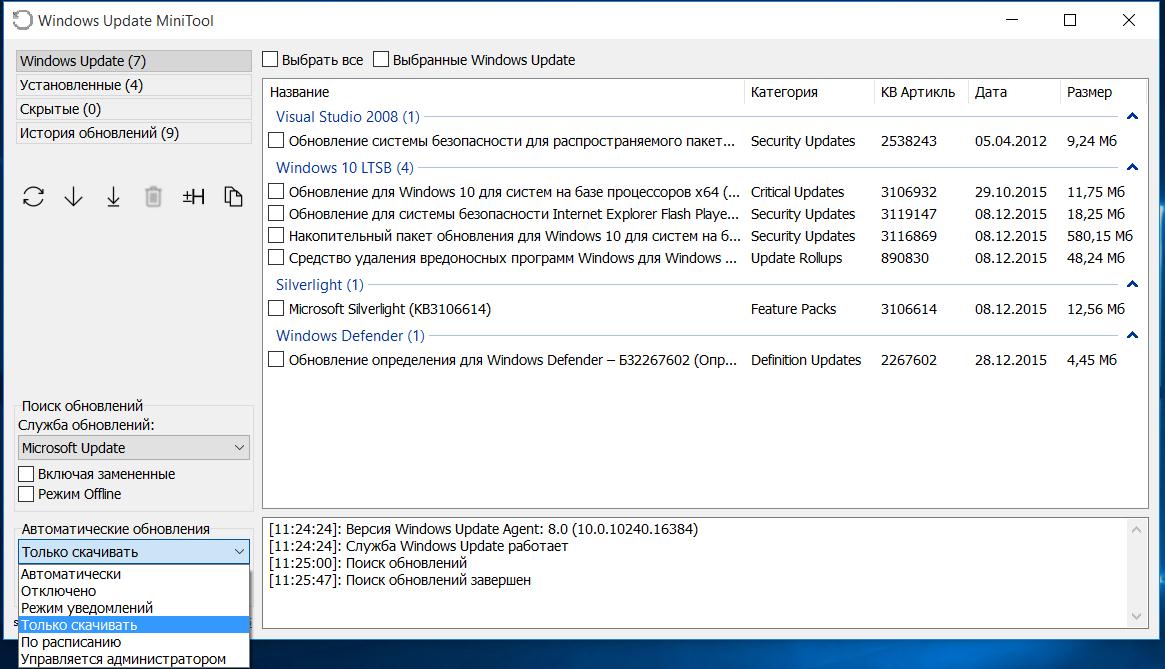
Просмотр новых обновлений:
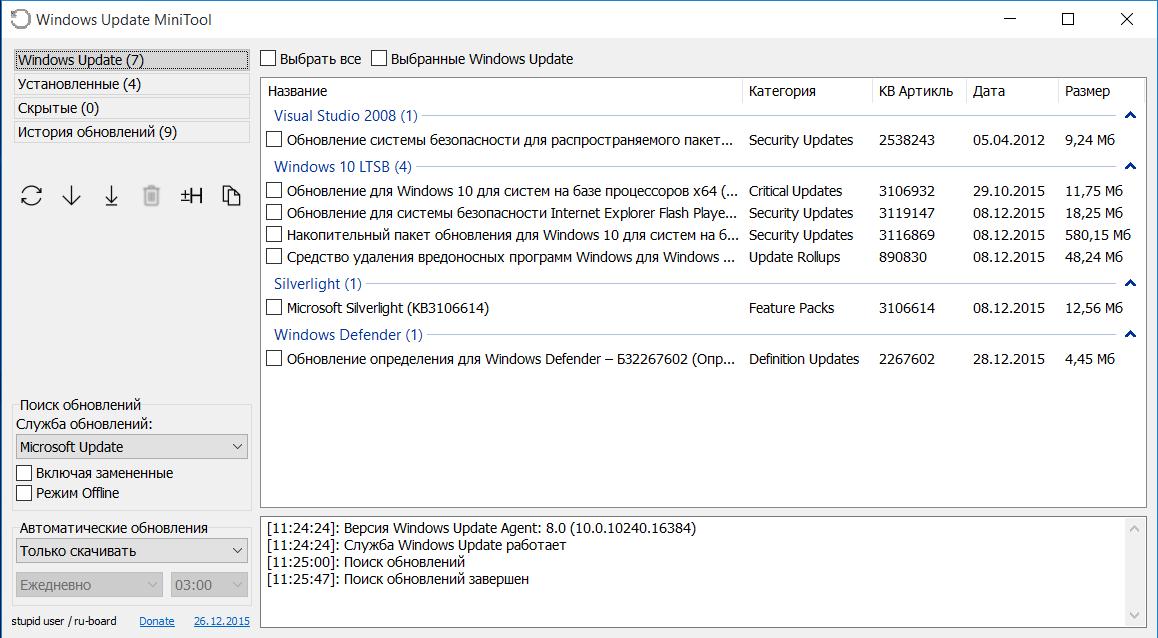 Просмотр уже установленных обновлений
Просмотр уже установленных обновлений 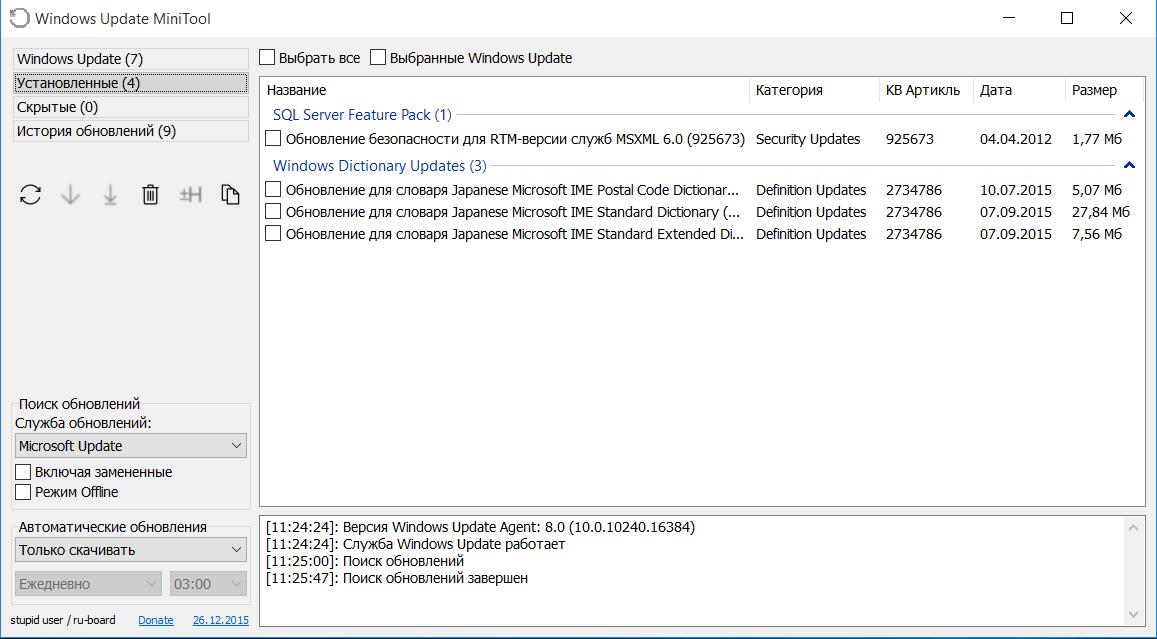
Просмотр истории обновлений:
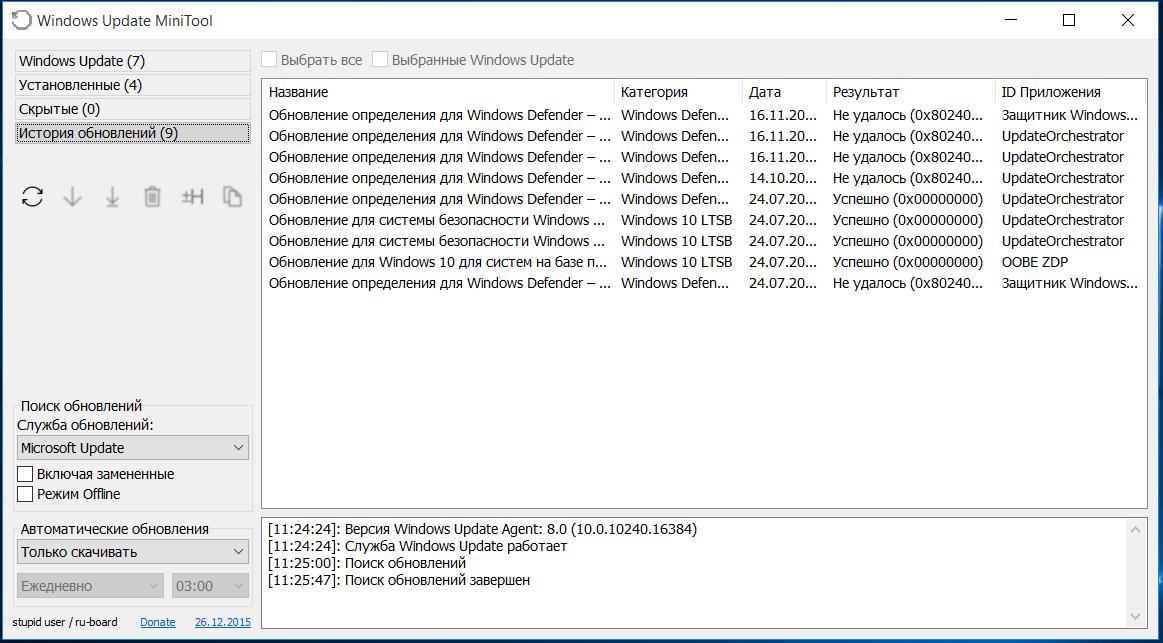
Таким образом, Windows Update MiniTool – это удобная и функциональная стронная утилита для управления службой обновлений в Windows, которая(практически незаменима для Windows 10.

How Windows Update works
The Windows Update workflow has four core areas of functionality:
- Scan
- Orchestrator schedules the scan.
- Orchestrator verifies admin approvals and policies for download.
- Orchestrator starts downloads.
- Windows Update downloads manifest files and provides them to the arbiter.
- The arbiter evaluates the manifest and tells the Windows Update client to download files.
- Windows Update client downloads files in a temporary folder.
- The arbiter stages the downloaded files.
- Orchestrator starts the installation.
- The arbiter calls the installer to install the package.
- Orchestrator starts a restart.
- The arbiter finalizes before the restart.
How updating works
During the updating process, the Windows Update Orchestrator operates in the background to scan, download, and install updates. It does these actions automatically, according to your settings, and silently so that doesn’t disrupt your computer usage.
Scanning updates
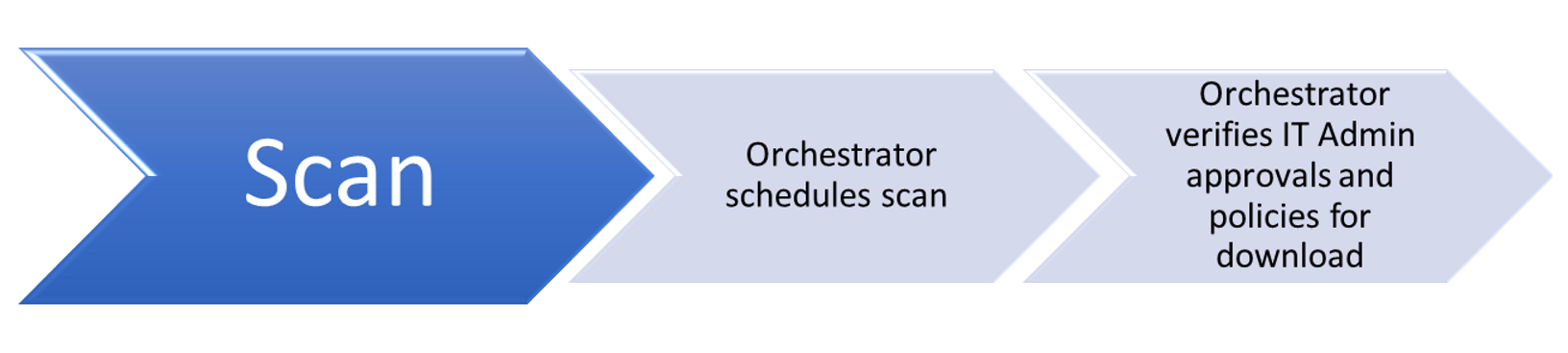
The Windows Update Orchestrator on your PC checks the Microsoft Update server or your WSUS endpoint for new updates at random intervals. The randomization ensures that the Windows Update server isn’t overloaded with requests all at the same time. The Update Orchestrator searches only for updates that have been added since the last time updates were searched, allowing it to find updates quickly and efficiently.
When devices check for updates, the Windows Update Orchestrator evaluates whether the update is appropriate for your device. It uses guidelines defined by the publisher of the update, for example, Microsoft Office including enterprise group policies.
Make sure you’re familiar with the following terminology related to Windows Update scan:
Term Definition Update We use this term to mean several different things, but in this context it’s the actual updated code or change. Bundle update An update that contains 1-N child updates; doesn’t contain payload itself. Child update Leaf update that’s bundled by another update; contains payload. Detector update A special update that contains IsInstalled applicability rule only and no payload. Used for prerequisite evaluation. Category update A special detectoid that has an IsInstalled rule that is always true. Used for grouping updates and allowing the device to filter updates. Full scan Scan with empty datastore. Delta scan Scan with updates from previous scan already cached in datastore. Online scan Scan that uses the network and to check an update server. Offline scan Scan that doesn’t use the network and instead checks the local datastore. Only useful if online scan has been performed before. CatScan Category scan where caller can specify a categoryId to get updates published under that categoryId. AppCatScan Category scan where caller can specify an AppCategoryId to get apps published under that appCategoryId. Software sync Part of the scan that only checks for software updates (both the apps and the operating system). Driver sync Part of the scan that checks driver updates only. This sync is optional and runs after the software sync. ProductSync A sync based on attributes, in which the client provides a list of device, product, and caller attributes ahead of time to allow service to check applicability in the cloud. How Windows Update scanning works
Windows Update does the following actions when it runs a scan.
Starts the scan for updates
When users start scanning in Windows Update through the Settings panel, the following occurs:
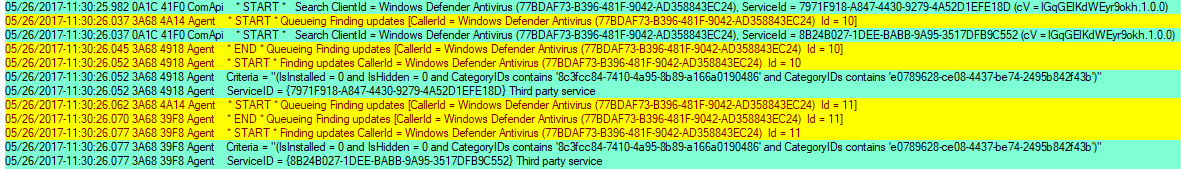
- The scan first generates a ComApi message. The caller (Microsoft Defender Antivirus) tells the Windows Update engine to scan for updates.
- “Agent” messages: queueing the scan, then actually starting the work:
- Updates are identified by the different IDs (“ID = 10”, “ID = 11”) and from the different thread ID numbers.
- Windows Update uses the thread ID filtering to concentrate on one particular task.
Proxy Behavior
For Windows Update (WU) scans URLs that are used for update detection (MS-WUSP: SimpleAuth Web Service, MS-WUSP: Client Web Service):
- System proxy is attempted (set using the netsh command).
- If WUA fails to reach the service due to a certain proxy, service, or authentication error code, then user proxy is attempted (generally it’s the logged-in user).
Note For intranet WSUS update service URLs, we provide an option via Windows Update policy to select the proxy behavior.
For Windows Update URLs that aren’t used for update detection, such as for download or reporting:
- User proxy is attempted.
- If WUA fails to reach the service due to a certain proxy, service, or authentication error code, then the system proxy is attempted.
Identifies service IDs
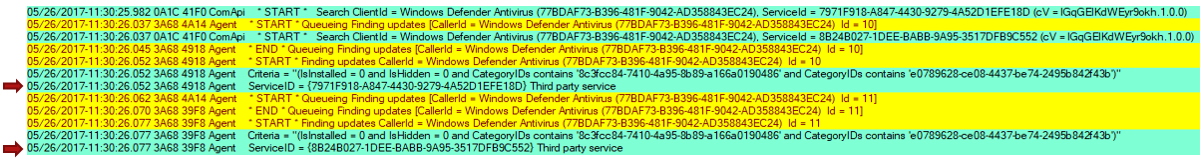
- Service IDs indicate which update source is being scanned.
- The Windows Update engine treats every service as a separate entity, even though multiple services may contain the same updates.
- Common service IDs
Important ServiceId here identifies a client abstraction, not any specific service in the cloud. No assumption should be made of which server a serviceId is pointing to. It’s totally controlled by responses from the Service Locator Service.
Finds network faults
Common update failure is caused due to network issues. To find the root of the issue:
- Look for “ProtocolTalker” messages to see client-server sync network traffic.
- “SOAP faults” can be either client- or server-side issues; read the message.
- The Windows Update client uses the Service Locator Service to discover the configurations and endpoints of Microsoft network update sources: Windows update, Microsoft Update, or Flighting.
Note If the search is against WSUS or Configuration Manager, you can ignore warning messages for the Service Locator Service.
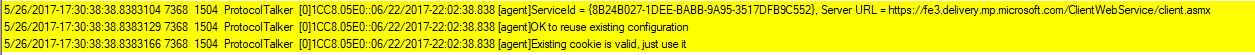
- On sites that only use WSUS or Configuration Manager, the Service Locator Service might be blocked at the firewall. In this case the request will fail, and though the service can’t scan against Windows Update or Microsoft Update, it can still scan against WSUS or Configuration Manager, since it’s locally configured.
Downloading updates
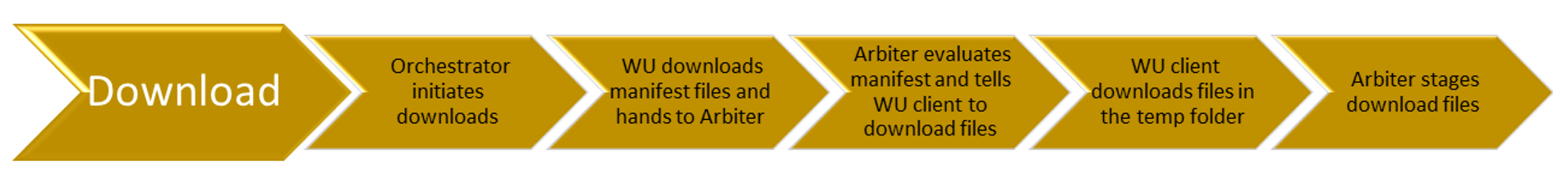
Once the Windows Update Orchestrator determines which updates apply to your computer, it begins downloading the updates, if you have selected the option to automatically download updates. It does operation in the background without interrupting your normal use of the device.
To ensure that your other downloads aren’t affected or slowed down because updates are downloading, Windows Update uses Delivery Optimization, which downloads updates and reduces bandwidth consumption.
Installing updates

When an update is applicable, the “Arbiter” and metadata are downloaded. Depending on your Windows Update settings, when downloading is complete, the Arbiter will gather details from the device, and compare that with the downloaded metadata to create an “action list”.
The action list describes all the files needed from Windows Update, and what the installation agent (such as CBS or Setup) should do with them. The action list is provided to the installation agent along with the payload to begin the installation.
Committing Updates
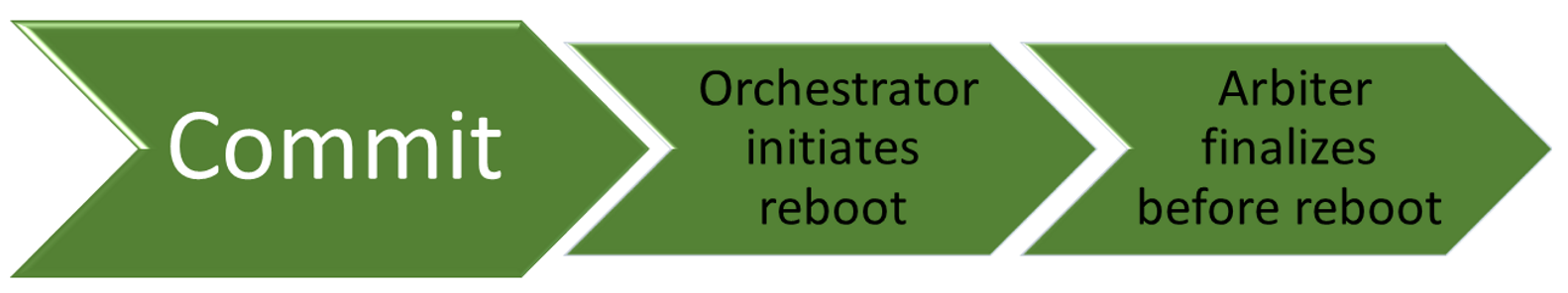
When the option to automatically install updates is configured, the Windows Update Orchestrator, in most cases, automatically restarts the device for you after installing the updates. It has to restart the device because it might be insecure, or not fully updated, until it restarts. You can use Group Policy settings, mobile device management (MDM), or the registry (not recommended) to configure when devices will restart after a Windows 10 update is installed.
Feedback
Submit and view feedback for
При подготовке материала использовались источники:
https://support.microsoft.com/en-us/topic/description-of-the-windows-update-standalone-installer-in-windows-799ba3df-ec7e-b05e-ee13-1cdae8f23b19
https://winitpro.ru/index.php/2015/12/30/utilita-windows-update-minitool/
https://learn.microsoft.com/en-us/windows/deployment/update/how-windows-update-works
 Онлайн Радио 24
Онлайн Радио 24 